Google is the encyclopedia of the internet that carries the reply to all your questions and curiosity. Just after all, it is just a web index to uncover photos, articles, and videos, appropriate?
Effectively, if you imagine so, you are turning a blind eye to the untapped prospective of the behemoth lookup engine’s crawling capabilities. This aspect of Google is lesser-regarded to the average user but propelled proficiently by undesirable actors to hijack websites and steal delicate info from companies.
Listed here, we are going to deal with how safety gurus and hackers use Google as an effective reconnaissance tool to access delicate information, hijack web sites, and more.
What Is Google Dorking?
Google dorking or Google hacking is the procedure of feeding state-of-the-art search queries into the Google look for motor to hunt for sensitive knowledge this sort of as username, password, log data files, and so forth., of web-sites that Google is indexing due to web page misconfiguration. This information is publicly noticeable and, in some circumstances, downloadable.
A typical Google look for requires a seed search phrase, sentence, or concern. But, in Google dorking, an attacker makes use of exclusive operators to boost search and dictate the web crawler to snipe for extremely distinct documents or directories on the world-wide-web. In most situations, they are log files or web site misconfigurations.
How Hackers Use Google Dorking to Hack Web-sites
Google dorking entails making use of special parameters and search operators called “dorks” to narrow down search benefits and hunt for uncovered delicate data and safety loopholes in web-sites.
The parameters and operators direct the crawler to search for particular file kinds in any specified URL. The lookup success of the query involve but are not limited to:
- Open FTP servers.
- A company’s interior paperwork.
- Accessible IP cameras.
- Federal government files.
- Server log documents that contains passwords and other delicate facts that can be leveraged to infiltrate or disrupt an business.
Most-Used Google Dorking Operators
While there are tons of operators and parameters that a single can utilize to a research query, it only requires a handful of them to provide the demands of a security experienced. Here are a several usually utilised queries:
- inurl: Dictates the crawler to research for URLs that have a specified search phrase.
- allintext: This parameter searches for consumer-specified text in a webpage.
- filetype: This parameter tells the crawler to search for and show a distinct file style.
- intitle: Scrapes for internet sites made up of specified keyword phrases in the title.
- internet site: Lists all the indexed URLs for the specified web site.
- cache: When paired with the website parameter, this a person displays the cached or more mature variation of a website.
- Pipe operator (|): This reasonable operator will list outcomes that comprise either of two specified research phrases.
- Wildcard operator (*): This is a wildcard operator that queries for web pages that consist of anything connected to your look for term.
- Subtract operator (-): This gets rid of unwanted final results from your search.
Is Google Dorking Illegal?
Although it may possibly seem to be overwhelming, Google dorking will not land you guiding bars, provided you are only applying it to refine your research benefits and not infiltrate an business.
It is a essential evil and, in reality, an encouraged exercise amongst power end users. Keep in thoughts that Google is tracking your queries all the time, so if you obtain sensitive facts or lookup with destructive intent, Google will flag you as a threat actor.
In case you are carrying out a pen exam or searching for bug bounty, make sure that you are entirely authorized and backed by the organization. If not, if you get caught, factors can get a convert for the worst, and one can even slap you with a lawsuit.
How to Protect Your Internet site From Google Hacking
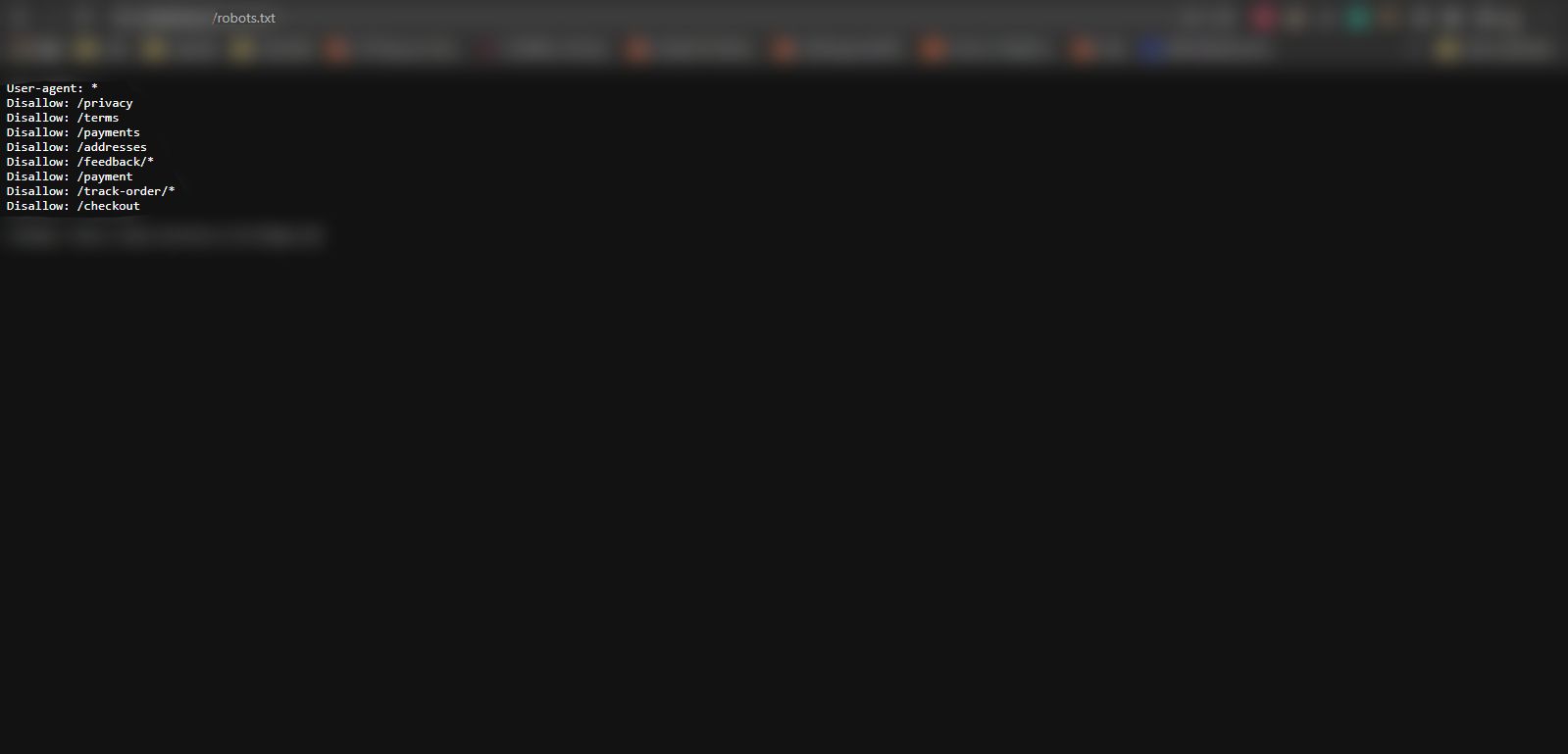
As a webmaster, you have to established up certain defensive countermeasures to tackle Google Dorking. A very uncomplicated technique would be to incorporate a robots.txt file and disallow entry to all delicate directories. This will hold research motor crawlers from indexing delicate files, directories, and URLs as you list them.
Incorporating a robots.txt file to the root listing is a common good follow and crucial for the general security of your web-site. Master much more about why web-site protection is critical.
Other ways to mitigate this threat would be to encrypt sensitive data such as usernames, passwords, payment facts, etcetera., and use Google Lookup Console to eliminate webpages from look for benefits.
Come to be a Google Ability User With Google Dorking
Although most of us use Google each individual day, we barely ever acquire benefit of its correct prospective. You can harness the usually-forgotten electrical power of Google dorking ethically to refine your Google-fu and come across just about everything on the online.
With the correct parameters and key phrases in put, the response to all your curiosities and concerns will lie at your fingertips, just 1 keypress away. Study far more about the finest tips and methods to make the most of your Google search.