[ad_1]

Scientists have unearthed a discovery that does not manifest all that normally in the realm of malware: a experienced, under no circumstances-prior to-found Linux backdoor that employs novel evasion approaches to conceal its existence on infected servers, in some situations even with a forensic investigation.
On Thursday, researchers from Intezer and The BlackBerry Threat Investigation & Intelligence Staff claimed that the beforehand undetected backdoor brings together higher concentrations of access with the potential to scrub any indicator of an infection from the file program, method procedures, and network targeted traffic. Dubbed Symbiote, it targets money institutions in Brazil and was initial detected in November.
Researchers for Intezer and BlackBerry wrote:
What helps make Symbiote different from other Linux malware that we generally appear throughout, is that it needs to infect other running procedures to inflict destruction on contaminated devices. As a substitute of currently being a standalone executable file that is operate to infect a machine, it is a shared object (SO) library that is loaded into all jogging procedures applying LD_PRELOAD (T1574.006), and parasitically infects the equipment. Once it has infected all the managing procedures, it gives the risk actor with rootkit features, the ability to harvest qualifications, and remote entry functionality.
With the support of LD_PRELOAD, Symbiote will load ahead of any other shared objects. That lets the malware to tamper with other library files loaded for an software. The impression under reveals a summary of all of the malware’s evasion strategies.
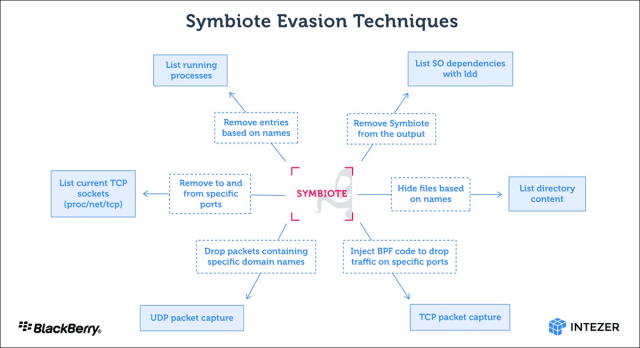
BPF in the picture refers to the Berkeley Packet Filter, which lets persons to conceal destructive community targeted visitors on an contaminated machine.
“When an administrator commences any packet seize instrument on the infected device, BPF bytecode is injected into the kernel that defines which packets must be captured,” the researchers wrote. “In this approach, Symbiote adds its bytecode initial so it can filter out community targeted traffic that it doesn’t want the packet-capturing application to see.”
A person of the stealth techniques Symbiote employs is recognized as libc perform hooking. But the malware also employs hooking in its purpose as a information-theft software. “The credential harvesting is performed by hooking the libc browse operate,” the researchers wrote. “If an ssh or scp course of action is calling the operate, it captures the qualifications.”
So much, there is no proof of bacterial infections in the wild, only malware samples observed on the net. It’s not likely this malware is commonly lively at the second, but with stealth this sturdy, how can we be certain?
[ad_2]
Resource link